
7 Ways Pen Testing for Education Boosts Cyber Security

If there’s anything we need to learn from this year, it’s that the ever-increasing threat of cybercrime underscores the critical need for enhanced network security. The education sector in particular has grown heavily reliant on technology and faces increased vulnerability due to inadequate security awareness and financial support. Cybercriminals exploit these weaknesses, jeopardising the privacy of staff, stakeholders and students. Intellectual property (IP) and personally identifiable information (PII) are constantly at risk. To tackle these challenges, pen testing for education is crucial, it’s the most effective strategy for identifying and addressing security gaps before malicious actors can exploit them, ensuring a resilient defence against potential cyber threats.
In this blog we aim to help education professionals develop a comprehensive understanding of network penetration testing and showcase how it can elevate their institution’s IT security capabilities cost-effectively. Before this blog dives into the benefits of network penetration testing, let’s establish what it is and the value it holds in safeguarding a school’s IT environment.
Did You Know?
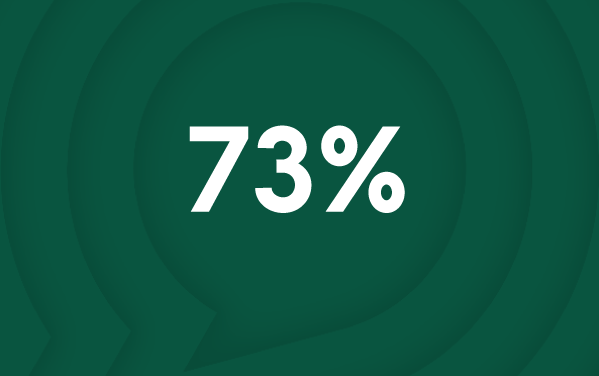
Cyberattacks have impacted 73% of the UK education sector over the past five years.*

One-third of the education institutions surveyed still lack basic security protections.*

Ransomware attacks have cost UK schools as much as £3 million per incident.**
What is Pen Testing for Education?
Network penetration testing, often referred to as pen testing or ethical hacking, is a proactive approach to uncovering and resolving weaknesses within your network infrastructure. During a pen test, security professionals simulate real-world cyberattacks to assess how well your systems stand up against modern threats.
The purpose is simple: identify vulnerabilities and remediate them before a malicious attacker can take advantage. It’s widely recognised as one of the most reliable and effective methods for evaluating an organisation’s true security posture.
There are two types of pen testing available: internal network penetration testing and external network penetration testing.
Internal pen testing assesses the strength of your internal network by identifying misconfigurations, outdated software, and potential lateral movement pathways, enabling proactive remediation and a strengthened security posture.
External pen testing conducts external threat simulations to evaluate the security of perimeter assets, including firewalls, VPNs, and web servers, ensuring robust defences against internet-facing attacks.
By highlighting gaps in your IT environment ahead of time, network penetration testing gives you the insight needed to stay one step ahead of cybercriminals and protect your organisation from preventable breaches.
Why is Pen Testing for Education Important?
Network penetration testing allows cyber security professionals, specifically ethical hackers, to simulate highly sophisticated and diverse cyberattacks and mimic the tactics of malicious actors to pinpoint potential weaknesses. By conducting controlled assessments, cyber security professionals can gain valuable insights into the effectiveness of existing security measures, ensuring that vulnerabilities are identified and addressed before they can be exploited.
Beyond risk identification, network penetration testing also plays an important role in empowering schools to enhance their cyber readiness. The findings from these tests highlight immediate security concerns and provide a roadmap for strengthening defences over time.
This process fosters a culture of ongoing vigilance, where educational institutions can adapt to emerging cyber threats and refine their ability to manage cyber risks.
Penetration testing further helps schools, colleges and universities meet various compliance requirements, like those set by the Department of Education (DfE) or an insurer, by demonstrating their commitment to maintaining the highest standards of data protection along with the quality of education.
The 7 Benefits of Pen Testing for Education?
> Risk Identification
Penetration testing proactively uncovers vulnerabilities and weaknesses within your network infrastructure before cybercriminals have the chance to exploit them.
> Security Improvements
The results of penetration testing offer clear insight into where security improvements are needed. With this information, educational institutions can strengthen their overall security posture and make informed decisions about future protection measures.
> Compliance Assurance
Many insurers and regulatory frameworks now require routine security assessments. Penetration testing enables schools, colleges, and universities to demonstrate compliance and meet these obligations with confidence.
> Data Protection
Penetration testing protects sensitive data by uncovering and resolving vulnerabilities that could otherwise allow unauthorised access.
> Faster Incident Response
Penetration testing replicates real-world cyberattacks, helping schools and colleges to strengthen and fine-tune their incident response plans.
> Improved Decision-Making and Cost Savings
Penetration testing delivers valuable insight that supports smarter strategic decisions around cyber security investment and resource allocation.
> Continuous Monitoring
Regular penetration testing creates a continuous cycle of improvement, giving schools ongoing visibility into the strength of their security measures. This proactive approach ensures defences are consistently adapted and refined to keep pace with emerging threats in an ever-evolving cyber security landscape.

The Process of Network Penetration Testing
Network penetration testing is like a fire drill for your IT environment. Just as drills reveal gaps in a building’s emergency plan, pen tests simulate cyberattacks to expose vulnerabilities in your network defences.
This controlled, proactive exercise allows schools and colleges to identify and remediate weaknesses before a real attack occurs, ensuring their IT infrastructure remains robust, resilient, and prepared against evolving cyber threats. Croft’s network penetration testing process includes:
1. Define Scope
Define the systems and network areas to be assessed and set clear rules of engagement along with any legal requirements before testing begins.
2. Information Gathering
Carry out an initial discovery phase to build a clear picture of the target environment. This includes mapping live IP ranges, confirming domain information, and outlining the overall network structure.
3. Vulnerability Scanning
Leverage our automated discovery tooling to pinpoint active devices, exposed ports, and running services across the estate. This process highlights any weaknesses or misconfigurations that could present security risks.
4. Threat Modelling
Evaluate the intelligence collected to determine the most likely routes an attacker could exploit. From there, we rank identified risks to ensure the most critical vulnerabilities receive priority attention.
5. Exploitation
Conduct controlled security assessments to validate identified risks and confirm potential exposure pathways. Simulate realistic threat scenarios to ensure our clients’ environments are prepared for real-world attacks.
6. Post-Exploitation
Evaluate the organisation’s resilience by sustaining controlled, authorised access during testing, mirroring how real threat actors attempt to remain present within an environment. Determine the potential scope of exposure and movement available to an adversary to better inform remediation efforts.
7. Analysis and Reporting
Review and validate the outcomes of the security assessment, capturing all key observations, including confirmed vulnerabilities and areas of potential data exposure. Deliver a clear, prioritised report outlining recommended remediation actions and strategic enhancements to strengthen the organisation’s overall security posture.
8. Remediation
Partner with the school, college or university IT department to remediate discovered vulnerabilities. Apply required security patches, harden system configurations, and implement corrective measures in alignment with Croft’s security standards.
9. Reassessment
Perform a post-remediation validation assessment to confirm that corrective actions were effective. Verify that all previously identified vulnerabilities have been fully resolved and meet Croft’s security compliance standards.
Strengthen Your School’s Cyber Security with Croft's Network Penetration Testing
Educational institutions are increasingly exposed to cyber threats, making proactive security measures essential. Network penetration testing is a critical tool that identifies vulnerabilities and strengthens systems, protecting sensitive data and preventing potential breaches before they happen.
Student records, research data, and other critical information are prime targets for cybercriminals, placing schools and universities at significant risk.
Penetration testing acts as a pre-emptive defence, helping institutions detect and remediate weaknesses before they can be exploited.
Beyond threat prevention, penetration testing also supports regulatory compliance. By demonstrating a clear commitment to data protection, schools, colleges and universities can meet required standards, mitigate legal and financial risk, and reinforce trust in their IT security practices.
If your institution takes cyber security seriously, partner with Croft to ensure you are protected from the devastating effects of cybercrime.
We offer both internal and external network penetration testing to help your school identify vulnerabilities and assess risks, leading to an improved cyber security posture.
For more information, download our guide ‘Penetration Testing for Schools’ or contact one of our experts about your cyber security challenges.
Contact a Croft expert
You are currently viewing a placeholder content from HubSpot. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More Information
Joanna Williams
As a member of the design and marketing team at Croft, my work focuses on developing marketing materials, crafting compelling copy, and managing our website. I joined the team at Croft just over a year ago, bringing with me 13 years of experience in the IT industry.