
AI-Generated Phishing Threats: 6 Ways to Defend Your Business

The digital threat landscape is evolving at an unprecedented pace, and phishing remains one of the most pressing concerns for organisations today. Cybercriminals are increasingly weaponising artificial intelligence (AI) to craft sophisticated attacks that bypass traditional defences and exploit human vulnerabilities with alarming precision. While AI-generated phishing threats present significant challenges, understanding these attacks and implementing robust countermeasures can position your organisation to defend itself effectively.
In this blog, we'll examine how attackers leverage AI in phishing campaigns, the implications for your business, and the practical steps organisations can take to protect their networks and data from these advanced threats.
The Numbers Don't Lie
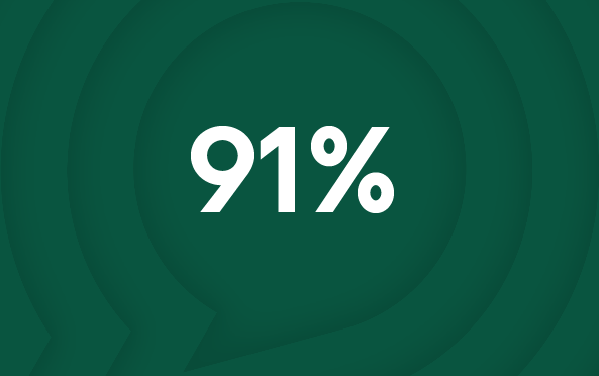
91% of cyber attacks begin with a phishing email*
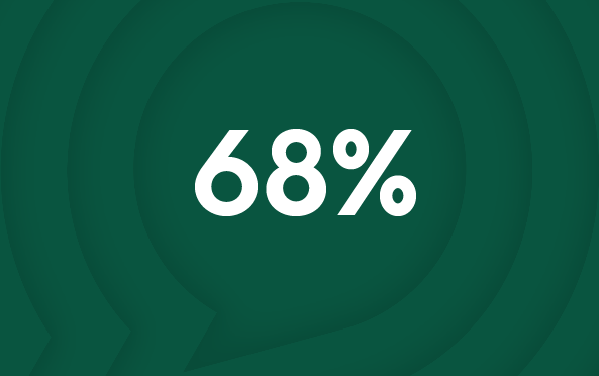
68% of data breaches involve the human element**

60% of businesses fail within 6 months of a significant cyber attack***
These statistics paint a sobering picture of the current threat environment. Phishing isn't just an IT problem; it's a business continuity risk that can have devastating consequences for organisations of all sizes.
How Attackers Are Weaponising AI-Generated Phishing Threats
Phishing has transformed dramatically from poorly crafted emails riddled with spelling errors to highly sophisticated, personalised campaigns that are increasingly difficult to detect. AI-generated cyber attacks are now the most feared threat by IT professionals and cyber security experts in 2025, and with good reason.
Today's attacks extend far beyond traditional email phishing to include smishing (SMS-based attacks) and vishing (voice phishing). Recent research shows that AI's performance in spear phishing improved by 55% between 2023 and 20254, with AI agents now outperforming top human security experts. This represents a fundamental shift in the threat landscape; attackers can now launch highly targeted campaigns with minimal effort and maximum impact.
Cybercriminals are exploiting AI tools like ChatGPT to generate authentic-sounding business communications that perfectly mimic your organisation's tone and style. They're deploying deepfake technology to replicate voices convincingly for vishing attempts, enabling them to impersonate executives during phone calls requesting urgent wire transfers. While creating realistic images and even video content that lends credibility to their schemes, making it nearly impossible to distinguish fake from genuine without careful verification.
The traditional warning signs of phishing (spelling mistakes, poor grammar, suspicious terminology, and generic greetings) are becoming obsolete. Modern AI-powered phishing emails are grammatically perfect, contextually relevant, and often contain accurate information about your organisation, your role, and your current projects. This makes detection increasingly challenging, even for security-aware staff.
6 Proven Tactics to Combat AI-Powered Phishing
Protecting your organisation against these evolving threats requires a comprehensive, layered approach that combines technology, processes, and people. Here are six essential tactics to strengthen your defences:
1. Implement Multi-Factor Authentication (MFA)
MFA remains one of the most effective security controls available. This straightforward additional verification step significantly reduces the risk of unauthorised access, even if credentials are compromised through phishing. By requiring multiple forms of authentication, something you know (password), something you have (phone or token), or something you are (biometric), you create a critical barrier that protects sensitive data and systems.
Even if attackers successfully phish a user's password, they cannot access accounts without the second factor. This simple measure can prevent the majority of credential-based attacks and should be implemented across all systems, particularly those containing sensitive data or providing administrative access.
2. Deploy AI-Powered Email Security Solutions
Modern email security platforms use artificial intelligence to detect, flag, and block sophisticated phishing attempts that traditional filters miss. These solutions analyse email patterns, examine content characteristics, assess sender behaviour, and compare messages against vast databases of known threats to identify suspicious communications.
By leveraging machine learning, these systems continuously adapt to new attack techniques, learning from each attempted breach to improve their detection capabilities. They can identify subtle anomalies in email headers, detect domain spoofing attempts, analyse the sentiment and urgency of message content, and flag requests that deviate from normal business patterns. This proactive approach provides a crucial first line of defence against AI-generated phishing campaigns.
3. Invest in Continuous Security Awareness Training
Your people remain your strongest defence and your greatest vulnerability. Senior executives are 23% more likely to fall victim to AI-driven, personalised phishing attacks due to their busy schedules and the trust placed in their authority5. This makes comprehensive, ongoing security awareness training essential for every member of your organisation, from the boardroom to the front line.
Implement regular training programmes that simulate realistic, AI-generated phishing scenarios. These hands-on exercises help staff recognise evolving threats, understand the tactics attackers use, and practice appropriate responses in a safe environment. Focus on teaching staff to slow down and verify unusual requests, particularly those involving financial transactions, credential sharing, or sensitive data access.
Establish clear protocols for verifying high-risk requests through a trusted second channel. For example, if an employee receives an email requesting a wire transfer or password reset, they should confirm the request through a phone call to a known number or an in-person conversation. Never reply to the suspicious email or call a number provided within it.
4. Utilise Behavioural Analysis Tools
AI-driven behavioural analysis monitors user activity to detect anomalies that may indicate a compromised account. These tools establish baselines of normal behaviour for each user (typical login times, usual locations, common file access patterns, and regular communication behaviours), then alert security teams to unusual patterns.
For example, if an account suddenly starts accessing files it has never touched before, logs in from an unexpected country, or begins sending emails outside normal working hours, the system can flag this activity for investigation. This enables swift intervention before damage occurs, potentially stopping attackers before they can exfiltrate data, deploy ransomware, or move laterally through your network.
5. Conduct Regular Security Audits
Routine security assessments help identify vulnerabilities in your systems and processes before attackers can exploit them. These audits should examine technical controls, review security policies, test incident response procedures, and assess staff awareness levels.
Incorporating AI-powered tools into these audits enhances their effectiveness, uncovering weaknesses that could be leveraged in phishing campaigns or follow-on attacks. Regular penetration testing, including simulated phishing exercises, provides valuable insights into your organisation's resilience and highlights areas requiring additional attention.
6. Participate in Threat Intelligence Sharing
The cyber security community's collective strength lies in collaboration. In 2025, effective cyber security isn't just about having robust firewalls; it's about outsmarting the machines trying to outsmart you. Sharing threat intelligence with industry peers and cyber security networks enables organisations to stay ahead of emerging phishing techniques and collectively strengthen defences against common adversaries.
By participating in information sharing initiatives, you gain early warning of new attack patterns, learn from others' experiences, and contribute to the broader effort to combat cybercrime. This collaborative approach ensures your organisation benefits from the combined knowledge and experience of the entire cyber security community.
Protect Your Organisation from AI-Generated Phishing Threats with Croft
As AI-powered phishing continues to evolve, a holistic cyber security strategy is no longer optional. It's essential for business survival. By combining advanced technology with comprehensive user education and proactive security measures, you can build resilient defences against today's sophisticated threat landscape.
At Croft, we understand the unique cyber security challenges facing businesses. Our comprehensive IT support and security solutions are designed to protect your organisation from emerging threats like AI-generated phishing attacks.
Don't wait until an attack succeeds. Contact Croft today to schedule a consultation with our team and learn how we can help protect your business from AI-powered phishing threats.
Sources
*ICO **Verizon ***Verizon Business

Joanna Williams
As a member of the design and marketing team at Croft, my work focuses on developing marketing materials, crafting compelling copy, and managing our website. I joined the team at Croft just over a year ago, bringing with me 13 years of experience in the IT industry.