
Threat Defence Security
Guard and remediate mobile devices from advanced cyber threats with Threat Defence Security that protects against endpoint, network, application and phishing attacks.
Mobile devices have become an essential business tool in today’s flexible workplace, allowing employees to access data from virtually any location. As a result, there is a growing issue that many users are accessing business critical data without robust security measures in place. Aware of this, cyber criminals are ready and waiting to take advantage of weak or non-existent mobile device security.
Croft’s Threat Defence Security (TDS) enables corporate and Bring Your Own (BYO) Android and iOS devices to be protected from advanced threats. It allows businesses to monitor, manage, and secure devices in real-time against threats including phishing and malicious web links.
Our TDS solution detects and remediates known and zero-day mobile threats even when a device has no available WiFi or mobile network. Additionally, you can be assured of 100% adoption, as no user action is required for activation.
Find out more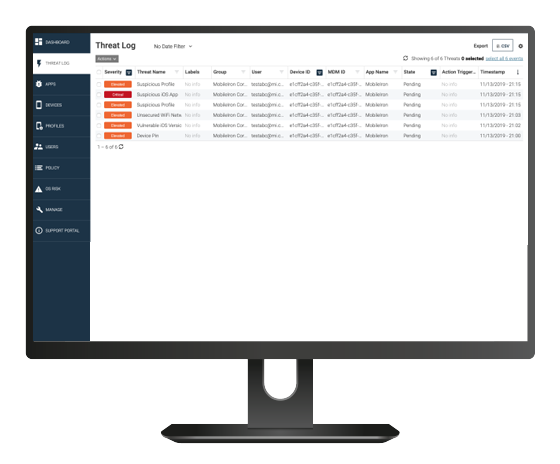
Threat Defence Security Benefits
Threat Defence Security Capabilities
Our TDS solution is powered by modern cyber security capabilities that help you to stay one step ahead of mobile threats. Our platform offers granular control and is further supported by a range of administrative features.

On-device Detection and Remediation
If a network connection is unavailable, on-device machine learning continues to secure endpoints from device, network, application or phishing attacks.
Find out more
Multi-vector Anti-phishing
On-device machine learning and phishing URLs are expandable to include cloud-based lookup, helping to boost the detection of threats. Using anti-phishing capabilities, TDS can spot and remediate phishing attacks across all mobile threat vectors, including email, text and SMS messages, instant messages, and social media.
Find out more
Proactive Remediation
Policy-based compliance actions alert admins to risky behaviours and proactively shut down attacks on-device. By isolating a compromised device, then removing the malicious application and its content, exploitation time is limited, helping to prevent zero-day attacks.
Find out more
In-depth Reporting
Intuitive dashboards and reports give full visibility and increased awareness into device, OS, network and application risks. This data offers actionable intelligence that increases effective response times to cyber attacks.
Find out more
Flexible Compliance
Additional compliance policies can be produced and enforced to prevent employees from disabling TDS or removing it from a device. Granular compliance controls can be initiated at server or device level supported with the ability to apply local remediation action configurations to different user groups.
Find out more
Unified Endpoint Management Integration (UEM)
To activate TDS on mobile devices, no user action is required if the device is enrolled on UEM, ensuring 100% user adoption.
Find out more
Granular Control
TDS offers admins granular control, allowing them to identify and remediate mobile apps that are in violation of your organisation’s compliance policies. Apps can be filtered using characteristics such as location tracking, SMS access, and screen recording. Risky behaviours can also be flagged and blocked, while security and risk reports support faster and more informed decision-making.
Find out moreThreat Defence Security in the Real World
TDS protects against device, network, application and phishing attacks. Here are some real-world examples of how you can easily become a victim of mobile threats.
- Device Exploitation – After an MMS message was sent to targeted users, a zero click chain exploit was triggered without user interaction. This launched a remote code execution that enhanced the attacker’s privileges, giving access to the targeted network.
- Network Attacks – While at a coffee shop a user experiences a WiFi man-in-the-middle attack which redirected them to a spear phishing page where company data was stolen.
- Malicious Apps – An unsuspecting user installed an app that subsequently misused permissions. This executed a device exploit, leaked data and was used to gain access to internal networks.
- Phishing Attacks – Using social engineering, an attacker tricked a user into clicking on a link and providing their login details, allowing them to log in as the user, enabling access to corporate data.

Experienced roaming bill shock?
If you are tired of paying exorbitant roaming fees when your employees travel abroad – and need something more than a basic travel SIM card for your enterprise travellers, look no further than Croft.
Find out more
Our Threat Defence Security Partners




Get in Touch
Contact our Croft experts to find out how our Threat Defence Security solution can ensure your mobile devices are protected from threats.
Get in touch
You are currently viewing a placeholder content from HubSpot. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More Information

