Unified Endpoint Management
Effectively manage and secure data across a wide range of mobile devices with Unified Endpoint Management (UEM). This single solution ensures your business remains productive and protected against malicious threats.
Securing devices spread across multiple locations and staying ahead of advanced threats can be a challenge for businesses of all sizes. To help maintain security and enhance productivity, it is important that organisations only allow compliant mobile devices to access their emails, apps, and data.
Our sophisticated UEM solution provides organisations with enterprise-level mobile management, monitoring and security that can keep pace with the modern work environment. Using a central platform, admins can manage, deploy, configure and monitor a range of mobile devices and apps. This allows businesses to balance allowing employees to use the devices they are most productive with and maintaining protection against advanced threats.
If your business is struggling with the security and management of its mobile devices, Croft’s UEM solution can help.
Find out more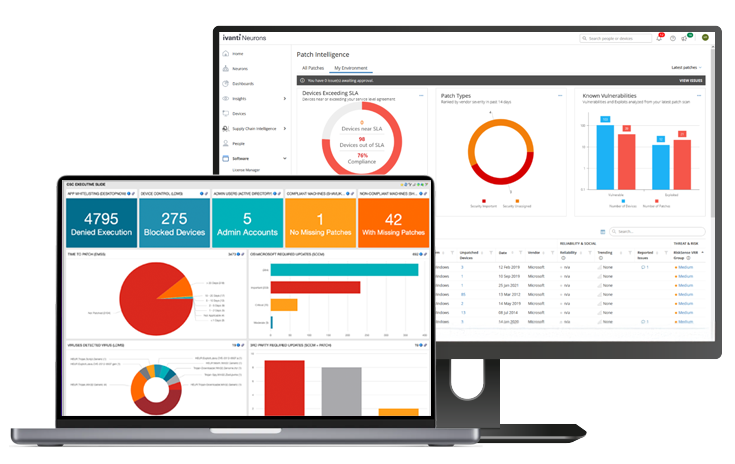
Unified Endpoint Management Benefits
Unified Endpoint Management Key Features
Croft’s UEM solution makes secure device management simple by using one platform that allows mobile devices to be tracked in real time. The key features of UEM include a central portal, remote management, increased security, customisable access and policies, data segmentation, seamless integration and automated tools. When combined in our UEM solution, these features support businesses to boost productivity, reduce IT complexity, and help maintain user experience across diverse endpoints.

Central Portal
UEM makes secure device management simple using our central platform that allows mobile devices to be tracked in real time regardless of their location.
Find out more
Remote Management
Admins can easily monitor, manage, and troubleshoot mobile devices via the UEM centralised portal. This helps to improve overall efficiency while reducing any device downtime.
Find out more
Security
Data is securely encrypted in transit between employees’ mobile devices and your corporate network. This ensures that data and networks are protected from a wide range of potential malicious threats.
Find out more
Customisable Access and Policies
Admins can create and enforce tailored access and security policies, along with troubleshooting any issues remotely. If a threat is detected, policies can promptly respond, preventing a user’s device from compromising your network.
Find out more
Data Segmentation
There’s no problem using Bring Your Own devices as corporate and personal data is easily segmented, allowing users to maintain their privacy while business data remains secure. Data is also secured in transit between employees’ mobile devices and your corporate network, ensuring that business and personal data remain separate
Find out more
Seamless Integration
UEM seamlessly integrates with your existing IT infrastructure and applications. This makes deployment completely stress-free for users and admins.
Find out more
Automated Tools
Policy and security updates can be applied using in-built automation tools within the UEM solution, ensuring all mobile devices remain compliant with industry regulations and corporate policies.
Find out moreUnified Endpoint Management or Threat Defence Security? Here’s Why You Need Both!
Unified Endpoint Management (UEM) and Threat Defence Security (TDS) are both essential tools for securing mobile devices, especially if your business has a Bring Your Own Device policy. When combined, they enable businesses to proactively manage and secure their mobile devices against the broadest array of threats, like malware, phishing, and network attacks.
Using centralised management, UEM provides the foundation for managing devices and security policies, while TDS provides real-time threat detection. Together they identify, remediate, and block threats before they can compromise your network.
If you would like to enhance the visibility of your mobile devices and increase the security posture of your business, find out more about our TDS solution.
Find out more
Experienced roaming bill shock?
If you are tired of paying exorbitant roaming fees when your employees travel abroad – and need something more than a basic travel SIM card for your enterprise travellers, look no further than Croft.
Find out more
Our Unified Endpoint Management Partners



Get in Touch
Contact our Croft experts to find out how our Unified Endpoint Management solution can ensure your mobile devices are protected from threats.
Get in touch
You are currently viewing a placeholder content from HubSpot. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More Information