IT Security Assessment
As cyber threats evolve, Croft’s IT Security Assessment helps UK organisations uncover risks and enhance security, aligned with Cyber Essentials.
Get in touchAs cyber threats grow with cloud and AI advancements, UK organisations face mounting security challenges. Croft’s IT Security Assessment offers a strategic review aligned with Cyber Essentials to uncover vulnerabilities, assess risks, and strengthen your cyber security posture.
In today’s rapidly evolving digital landscape, managing cyber threats and minimising the impact of breaches is essential for UK organisations, whether you're a small business or a large enterprise.
To stay secure, UK businesses are increasingly:
- Adopting Best Practices: Implementing proven cyber security strategies to reduce risk.
- Driving Continuous Improvement: Regularly reviewing and enhancing their security posture.
- Aligning with Government Standards: Following frameworks like Cyber Essentials to meet compliance and build trust.
Croft’s IT Security Assessment is designed to support these efforts by delivering deep insights and actionable intelligence. Our approach is fully aligned with the Cyber Essentials framework, helping you assess and strengthen your defences across the five key control areas.
Want to protect your business? Book your IT Security Assessment today
You are currently viewing a placeholder content from HubSpot. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More InformationSecurity Backed by a Team of Specialists
Croft’s comprehensive IT Security Assessment enables businesses to precisely understand their cyber security posture and prioritise actions to safeguard their IT environment.
Our dedicated cyber security professionals utilise advanced security software to uncover vulnerabilities hidden within your organisation's digital ecosystem. These specialists don't simply identify threats—they collaborate closely with your team to implement robust solutions that patch vulnerabilities and establish lasting protection against evolving cyber threats.
The powerful combination of advanced assessment technologies and our seasoned security experts delivers the ultimate peace of mind.
Rest assured knowing your valuable digital assets receive continuous protection from both existing and emerging threats in today's complex threat landscape.

What the IT Security Assessment Covers
Our assessment includes a comprehensive scan of your on-premises infrastructure, Microsoft 365 environment, dark web and external-facing systems. We utilise advanced tools and expert analysis to deliver:

Cyber Risk Assessment
Simulates real-world attack scenarios to identify vulnerabilities and recommend improvements

Baseline & Consolidated Security Reports
Summary of issues benchmarked against industry best practices and endpoint-level grading of antivirus, firewall, patching, and OS support.

External Vulnerability Scan
Identifies exploitable weaknesses in internet-facing systems.

Microsoft Cloud Risk Report
Highlights misconfigurations and risks in Azure AD and Microsoft 365.
Benefits of our IT Security Assessment
What You’ll Receive
Our security review provides a detailed evaluation of your organisation’s information technology safeguards.
We begin with an executive overview that highlights key security concerns, business implications, and areas for improvement. Our team examines system configurations, reviews security controls, and assesses user access management throughout your IT environment.
We identify opportunities to strengthen compliance with relevant industry standards and regulatory frameworks.
The accompanying improvement plan presents practical recommendations with clear ownership and realistic timelines for implementation. Our strategic insights help build long-term security capabilities that support your business operations.
We communicate our findings clearly and collaborate on establishing next steps for your ongoing security journey.
Summary Review
• Recap the purpose of the assessment • Highlight major findings in plain language • Emphasise business impact (e.g., risk to operations, compliance gaps)
Risk and Security Posture
• Discuss the Network Risk Score and what it means • Review top vulnerabilities (e.g., outdated software, open ports, weak passwords) • Explain potential threats (e.g., ransomware exposure, phishing, external ports etc.)
Infrastructure Overview
• Present the Asset Inventory: devices, operating systems, and software • Identify unauthorised or unknown devices • Highlight ageing or unsupported hardware
User and Access Management
• Review Active Directory findings: stale accounts, group memberships • Discuss login anomalies or risky user behaviours • Recommend access control improvements
Compliance and Data Exposure
• Review findings from the Data Breach Liability Report • Discuss any compliance concerns (e.g., GDPR, PCI-DSS) • Recommend data protection strategies
Remediation Plan
• Present a prioritised list of actionable insights • Discuss timelines, responsibilities, and potential costs • Offer managed services or support options if applicable
Strategic Recommendations and Roadmap
• Suggest long-term improvements (e.g., network segmentation, MFA, endpoint protection) • Propose regular assessments or continuous monitoring • Align IT strategy with business goals
Q&A and Next Steps
• Invite questions and clarify technical points • Agree on next steps: remediation, follow-up assessments, or service improvements
Our IT Security Assessment Process
Cyber security threats evolve rapidly and can devastate any organisation through financial losses, regulatory penalties, and reputation damage. Our comprehensive IT Security Assessment identifies vulnerabilities before they become costly problems, evaluating your entire IT infrastructure to ensure protection against current and emerging threats.
Phase 1: Data Collection and Scanning Automated scans of your IT environment to gather security data.
Phase 2: Expert Analysis Internal review of findings to identify critical risks and compliance gaps.
Phase 3: Reporting and Recommendations We present a clear, jargon-free summary of findings and guide you through next steps with expert advice.
Find out more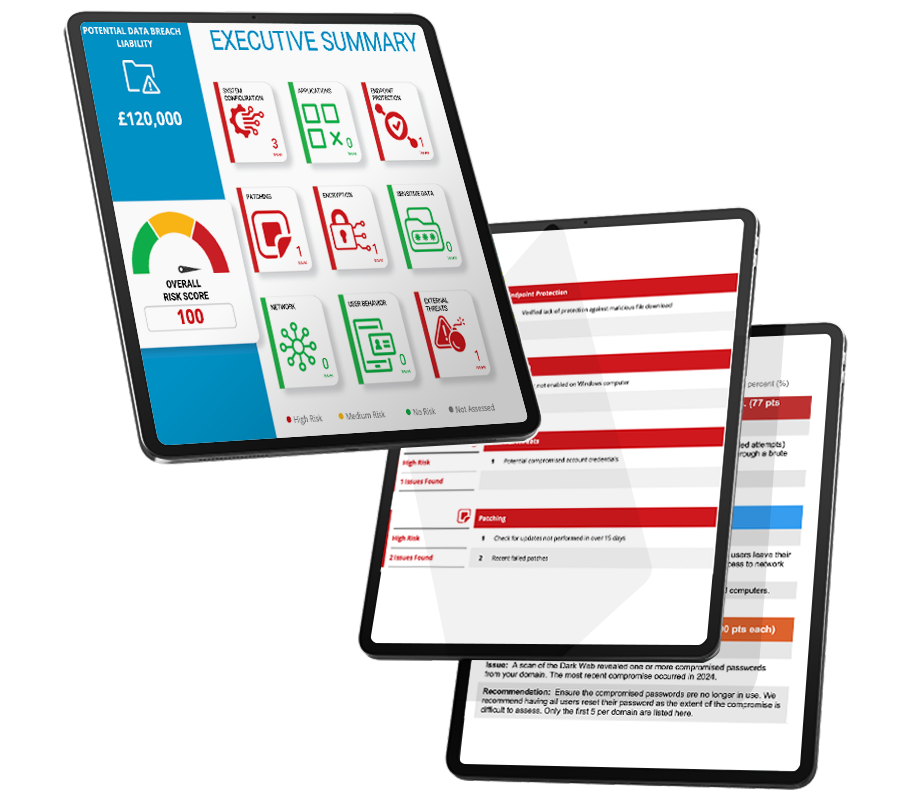
Cyber Essentials Alignment
Our assessment directly supports the five key Cyber Essentials controls:
- Firewalls –Evaluate perimeter defences and external vulnerabilities.
- Secure Configuration – Review endpoint and cloud settings to ensure alignment with best practices.
- User Access Control – Assess identity and access management in Microsoft 365.
- Malware Protection – Evaluate the protection, deployment, and effectiveness across devices.
- Security Update Management – Identify missing patches and unsupported systems.

Accreditations










Testimonials
What our clients say
Discuss challenges. Get Solutions
Speak to one of our IT Security Assessment specialists about your technology challenges.
Get in touch
You are currently viewing a placeholder content from HubSpot. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More Information