Pen Testing
Automated network pen testing that assesses your overall security posture before cyber criminals can.
Get in touchSpot vulnerabilities before hackers do – with CREST Certified, automated penetration testing. In a world where 56% of internet traffic is linked to criminal activity, the most effective defence against cybercrime is a strong and proactive offence.
Penetration testing (or pen testing) is a controlled method for assessing your cyber defences. Think of it as ethical hacking. Pen testing simulates what could happen if a hacker gains access to your network. It is used to identify vulnerabilities in your systems before cybercriminals can exploit them.
Advanced software performs a controlled security evaluation that simulates adversarial tactics to evaluate the resilience of an organisation’s IT infrastructure. This process is fully automated and designed to identify exploitable vulnerabilities in internal networks, as well as external firewalls and routers.
Croft’s partnership with Vonahi Security enables us to provide Council of Registered Ethical Security Testers (CREST) certified penetration testing, simulating real-world cyberattacks to identify vulnerabilities in your IT environment. Using these insights, you can validate your defences, minimise potential cyber risks, and ensure compliance with regulatory requirements. An in-depth assessment is performed that simulates real-world attack vectors—such as lateral movement, privilege escalation, and credential harvesting—to determine whether unauthorised access can be achieved. It evaluates firewall configurations, exposed services, patch levels, and authentication mechanisms, providing detailed insights into potential attack paths.
The objective is to proactively detect and remediate weaknesses before they can be leveraged by threat actors. vPenTest delivers comprehensive reports with CVSS scoring, exploitability analysis, and remediation guidance, helping IT teams prioritise fixes and maintain compliance with standards like PCI-DSS, HIPAA, and ISO 27001.
If your business takes its cyber security seriously, partner with Croft to protect your business from the devastating effects of a data breach.
Want to protect your business? Talk to us about pen testing today!
You are currently viewing a placeholder content from HubSpot. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More InformationBenefits of our Pen Testing
Pen Testing Services
In partnership with Vonahi Security we offer two different types of network penetration testing services. These solutions will help your business to identify vulnerabilities, access risks, and achieve a better cyber security posture and strategy.
Our automated network penetration testing can be scheduled at any time and can cost up to 60% less than a comparable traditional or manual test. Whether you require internal or external network penetration testing, you can be assured of receiving actionable insights that support the development of a more resilient cyber security program.

Internal Network Pen Testing
Using a device connected to your internal environment, our penetration test will discover security vulnerabilities present within the internal network environment. These activities simulate those of a malicious attacker.
Find out more
External Network Pen Testing
Assuming the role of a malicious attacker from the public Internet, our penetration test will identify security flaws within your external network environment.
Find out more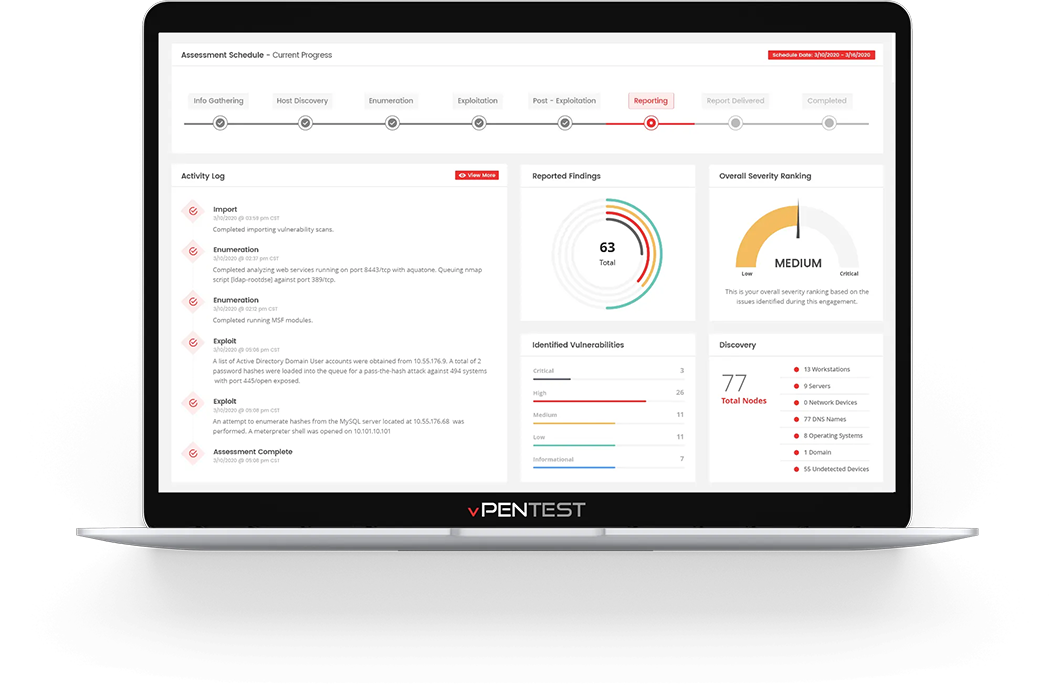
Continuous Automated Pen Testing
Our penetration testing allows you to test your network either monthly or as new threats emerge. Tests can be quickly scheduled, offering real-time tracking of your business’s risk profile.
Our intuitive reports will help you to analyse test results and identify ways to protect your valuable data by reducing your business’s attack surface.
Find out more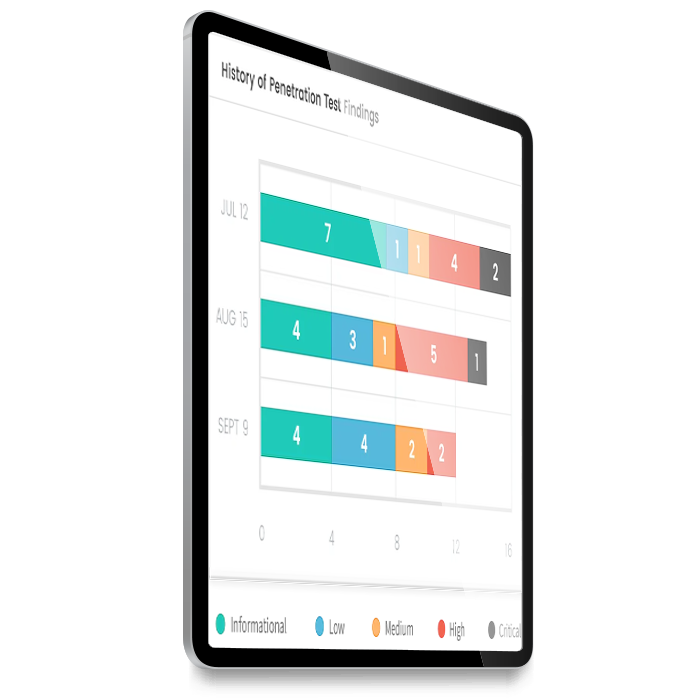
Pen Testing that Gives Real-time Visibility of Threats
Our real-time activity log can combine with your SIEM and incident response procedures to give a holistic view of security events as they happen.
As your live network penetration test is conducted, gaps in your monitoring controls will be highlighted for remediation.
Find out more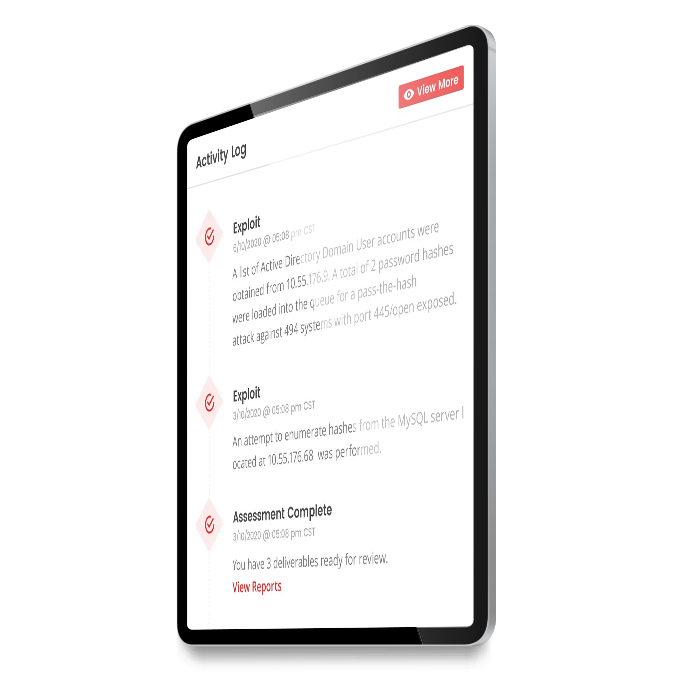
Accreditations










Testimonials
What our clients say
You might also be interested in ...
IT Security Assessment
Find out moreSecurity Awareness Training
Find out moreDiscuss challenges. Get Solutions
Speak to one of our pen testing specialists about your technology challenges.
Get in touch
You are currently viewing a placeholder content from HubSpot. To access the actual content, click the button below. Please note that doing so will share data with third-party providers.
More Information